
Top 3 Small Business Risks To Be Aware Of
Protect Your Business From Risk
Check out our options and create the perfect insurance plan. Get your free quote now.
Employee Fraud
Did you know that small businesses are the most common victim of fraud, with a fraud instance rate of 31.8%? Or that small businesses lost almost twice as much per fraud scheme as their larger counterparts?

Source: Association of Certified Fraud Examiners
Whether we can attribute that to fewer fraud prevention measures or less oversight, there is probably no one cause or origin. Fraud is a threat to any organization, but it’s one of the most significant small business risks you’ll encounter.
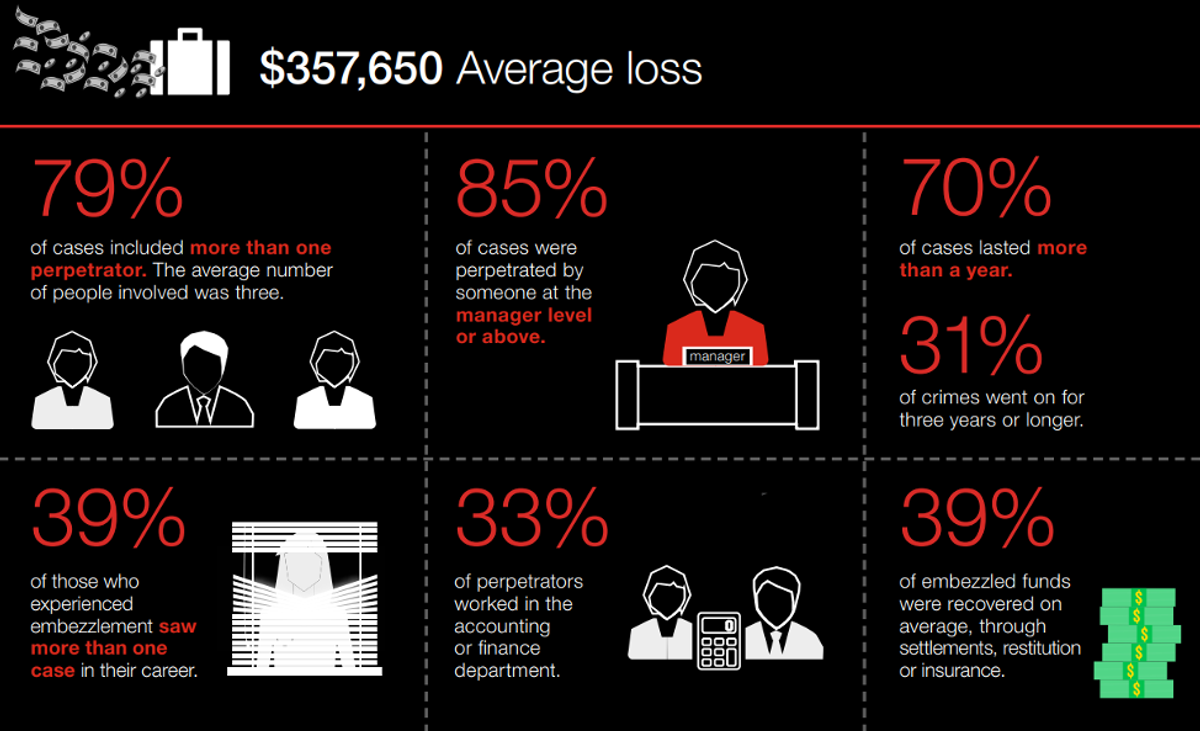
Source: 2018 Hiscox Embezzlement Study
Fraud schemes can range from a variety of different job functions and tasks across the company.
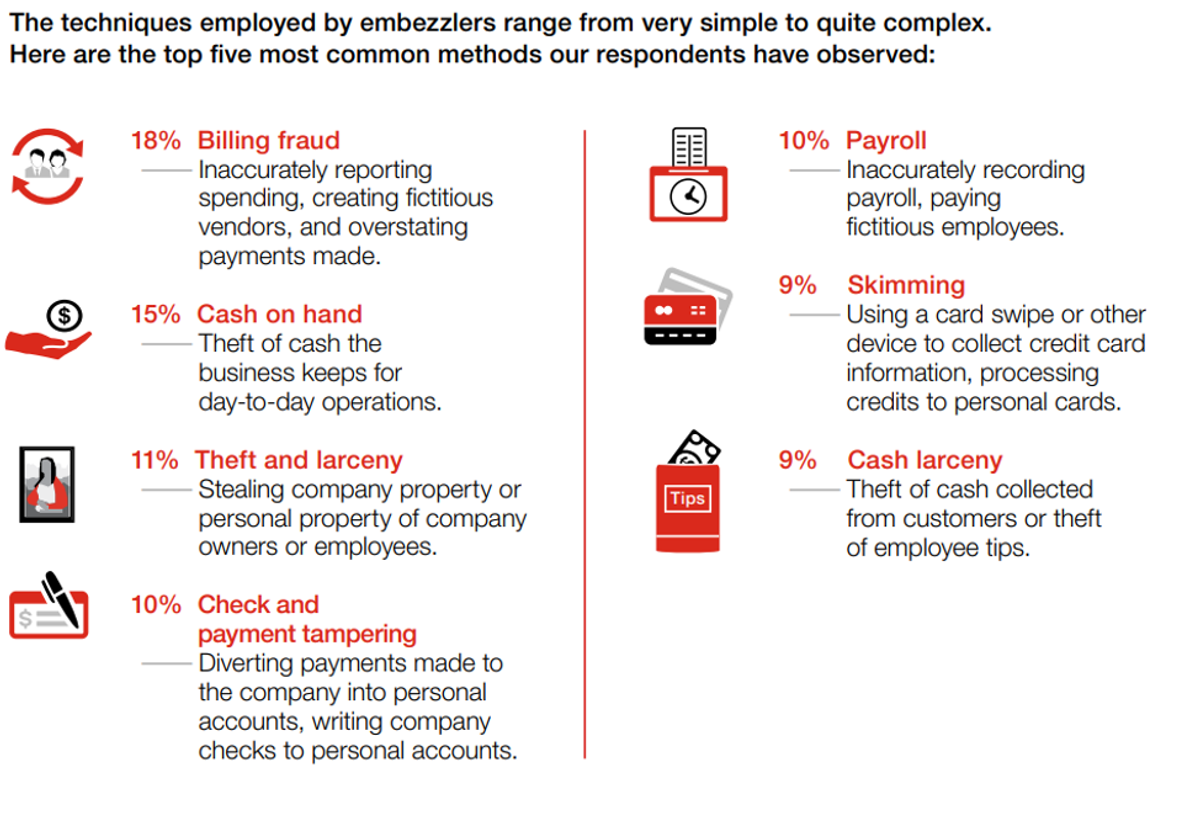
Source: 2018 Hiscox Embezzlement Study
How do I prepare my business?
Tip System: Tips are your first and strongest line of defense against fraud. Create a safe and easy way for employees and outside parties to report any fraudulent activities they see.
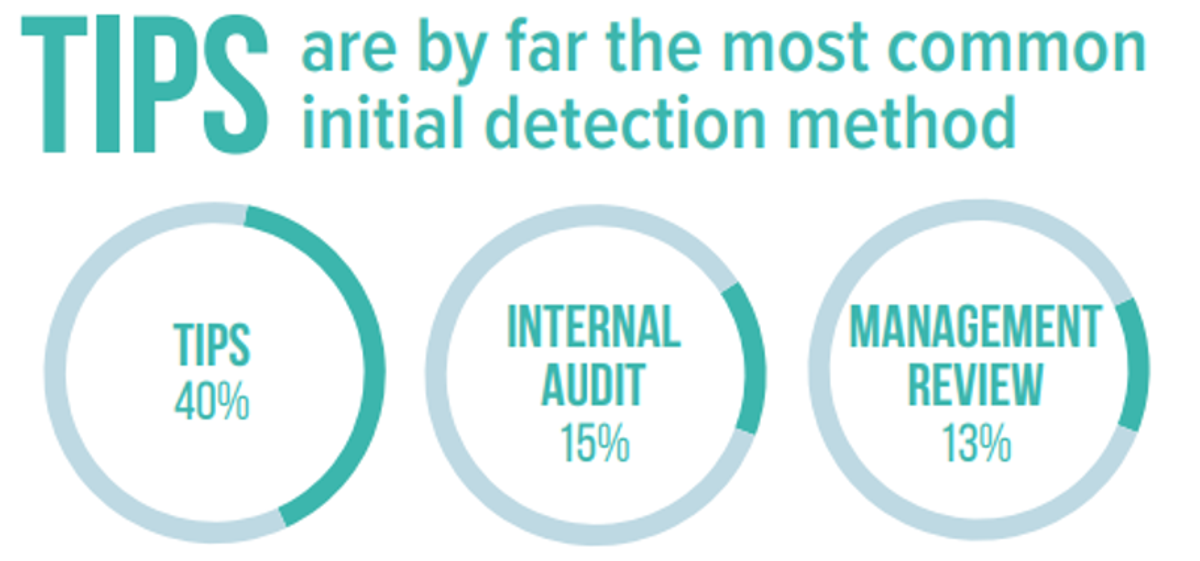
Source: 2018 Report to The Nations
Fraud Controls: Although receiving a tip is the top initial detection method, there are other controls you can implement that will greatly reduce your chances of becoming a victim of fraud. Internal audits, management reviews, document examinations, account reconciliation, and IT controls are just a few examples.
Employee Fraud Insurance: Although being proactive can substantially reduce your chances of becoming a victim of fraud, some situations can slip through the cracks. Employee fraud insurance will reimburse your company for unrecoverable amounts of money stolen from your organization.
Cybercrime
From credit card use and auto drafts to electronic funds transfers, nearly every business in every industry transfers money through electronic means. Criminals have caught on to this and are defrauding companies at an alarming rate, making cybercrime one of the biggest risks of running a business.
Cybercriminals pull off attacks using a couple of methods:
Social Engineering: An attacker tricks an employee of your business into either sending them money or releasing login information for a business platform. The attacker frequently disguises themselves as an executive or client of the company and reminds the employee of an outstanding invoice.
Here is an example of a social engineering email we received not too long ago that impersonated one of our executives.
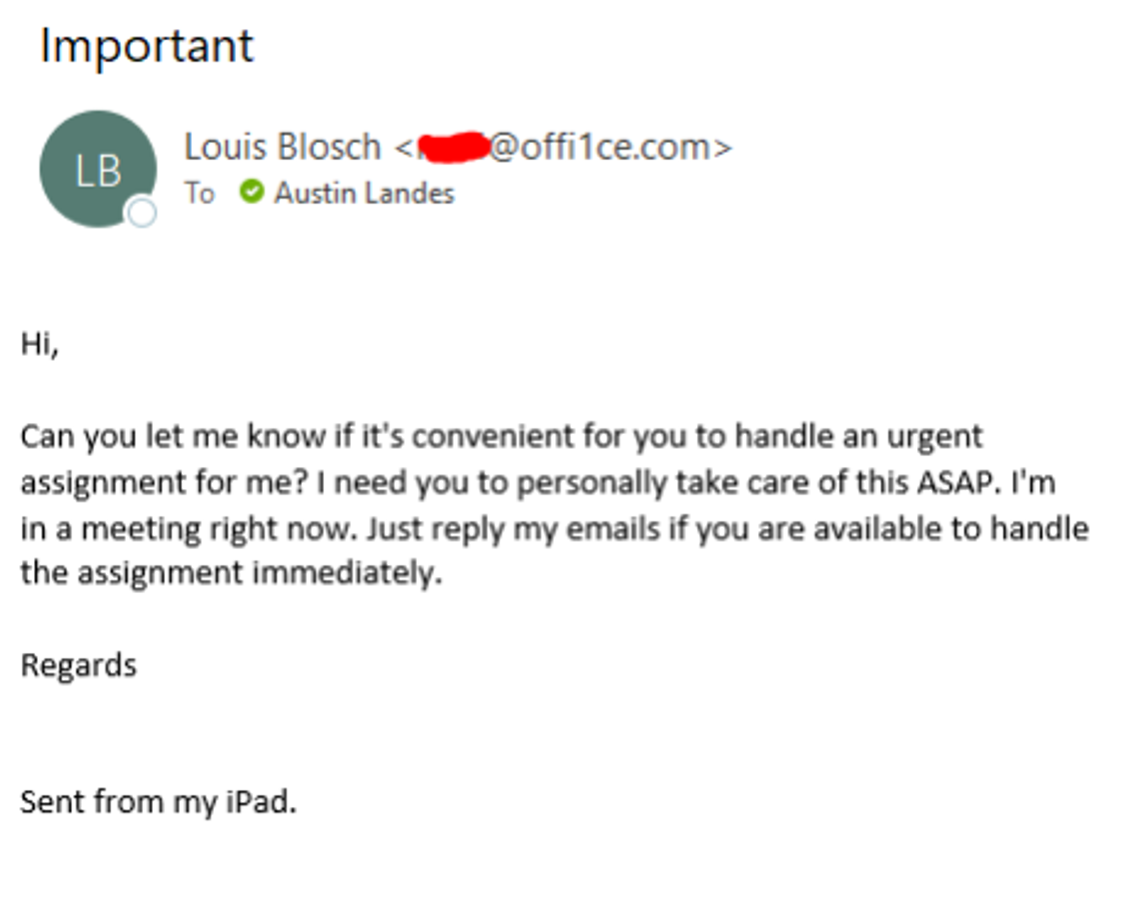
Notice how the email address is fraudulent, even though it says it is from “Louis Blosch.”
Also, notice how they are avoiding a phone call and are relying on email correspondence.
Although we would never reply to this email, if we did, the attacker would most likely respond asking us to send some money or conduct some other fraudulent activity.
A social engineering attack could also be a standard looking email that appears to be from Microsoft, but it is a fraudulent look-alike intended to trick you into entering your login information - resulting in an email breach.
Other popular scams are emails pretending to be from the IRS and fraudulent DocuSign links.
Electronic Compromise: This is probably what comes to mind when you imagine a typical hacking event. An attacker gains access to your network, servers, banking services, and information to wire themselves money or valuable data.
Electronic compromise could be especially dangerous to your organization if you have HIPAA information.
Extortion: When an attacker gains access to your computer system they will frequently try to extort you for money. Whether they threaten to delete your data or leak it into the public, usually there is a monetary demand (often in cryptocurrency) to make the problem go away.
How do I prepare my business?
Employee Training: A successful social engineering attack depends on your staff failing to recognize and avoid a scam. Proper training can significantly reduce the chances of an attacker fooling one of your employees into wiring them money or giving up sensitive credentials.
Feel free to use our employee cyber training material! Employee Cyber Training - Instruction GuideEmployee Cyber Training - Overview & Best PracticesEmployee Cyber Training - CommunicationCyber Employee Training - Devices
2-Factor Authentication: 2-Factor Authentication or Multi-Factor Authentication is a way to protect your business from attackers that should not be in your computer system, email, and bank accounts.
In a bulletin from CFC Underwriting titled “Client Advisory: Implementing multi-factor authentication is critical,” the process is explained as
“… an authentication process that is used to ensure that a person is who they say they are by requiring a minimum of two pieces of unique data that corroborates their identity.”
These two forms of authentication can be multiple forms of identification. For example, when logging into your email, the email provider could send a text to your cellphone that gives you a code to enter on your desktop. This second form of identification (your cellphone) requires more information than the attacker usually has access to.
Incident Response Plan: You can significantly reduce your chances of getting hacked by using the advice above, but sometimes you can't avoid everything.
Having a cyber incident response plan can help you minimize non-operational time and help you reduce monetary damages.
Cyber Insurance: When all else fails, you can buy insurance for cyberattacks. Not only will a policy like this pay for the liability associated with the breach (leaking private information), but it will pay your costs associated with getting your business operational again and avoiding an incident in the future.
A cyber policy does more than pay for the costs associated with an attack, though. A quality cyber insurance policy will provide you with experts to investigate the attack and guide you through the tough process of getting your business back on track.
Natural Disasters
In a previous insight, “Business Interruption Insurance - What's Covered,” we mentioned that 40-60% of small businesses never reopen their doors following a disaster.
This is a huge problem and one of the largest risks of owning a small business; after all, if you’re open long enough, you will experience some interruption event, whether it is a natural disaster, a fire, or even a cyberattack.
Do you have a plan to keep your doors open? Do you have the cash reserves to pay your bills and make payroll for an extended period of time?
The solution could be easier than you think.
How do I prepare my business?
Business Continuity Plan: A business continuity plan is a written plan that details the procedures that you will complete if a disaster strikes.
This plan outlines supply chain concerns, communication plans, and how to continue operations.
Obtain Necessary Insurance: By purchasing business income and extra expense insurance, you can transfer the financial risk of shutting your doors to an insurance
company.
This policy will pay for your ordinary expenses and net income while your business is recovering from the disaster.
It will also pay for most extra expenses resulting from relocating your business to a temporary location.
Summary
There are many small business risks that you will face, some greater than others. Taking a proactive approach to managing these risks will reduce the severity of an event. As you grow, it’s up to you to decide if you want to transfer the risk altogether to an insurance company for a reasonable price.
Want to learn more about transferring your risk? Contact us today!
About The Author: Austin Landes, CIC
Austin is an experienced Commercial Risk Advisor specializing in property & casualty risk management for religious institutions, real estate, construction, and manufacturing.
