
The Real Cyber Risk
If you are like most small to medium sized businesses in America, you do not have a team of cybersecurity experts on staff. Even though nothing can replace such a group, there are steps you can take not to become another headline.
Despite what sensational reporting would lead you to believe, "hacking" is not the only source of data breaches in US companies. According to Chubb, a sizeable cyber insurance company, hacks only accounted for 34% of their overall cyber claims in the past three years. Although cutting edge network equipment and security software may be the most obvious solution, such tools should only be one aspect of your overall risk management plan.
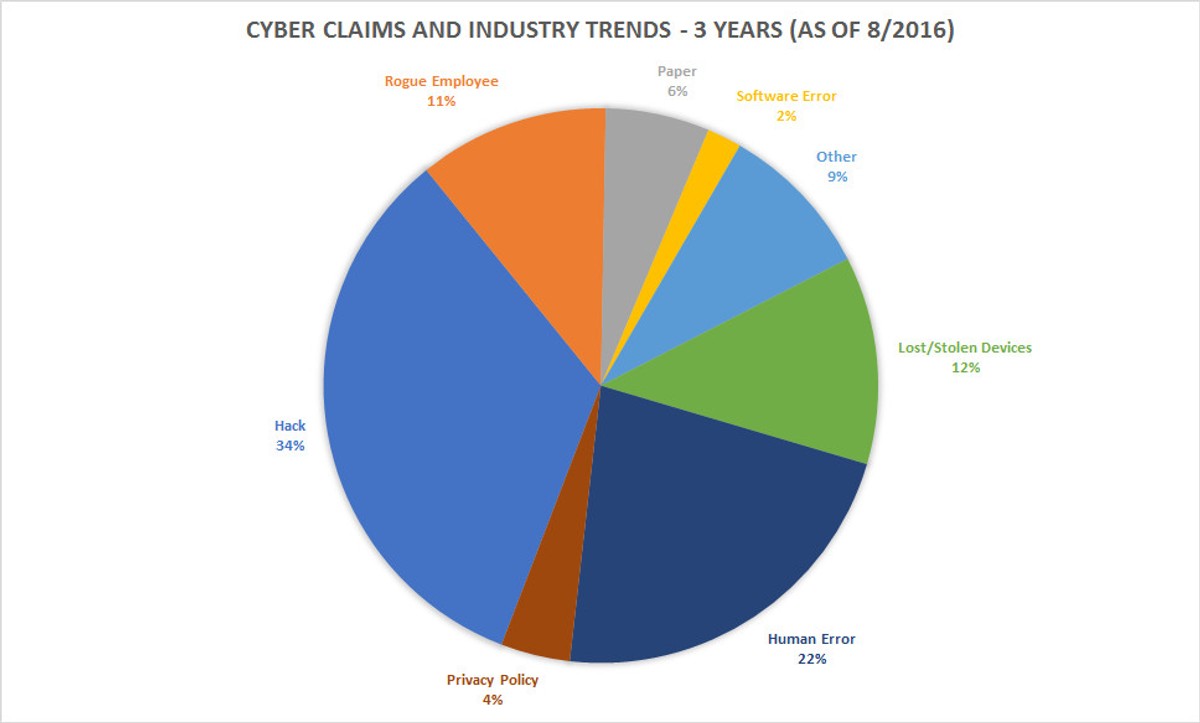
As you can see from the chart above: rogue employees, human error, and lost/stolen devices account for nearly 45% of all security breaches. With this trend in mind, the greatest threat organizations face today are not malicious hackers, but from within.
What Can I Do About It?
1) Encrypt your devices
If an employee device were to be lost or stolen, the first line of defense would be encryption. Data is useless to an attacker or intruder if the data compromised is in a broken format. Brute-force hacking a 128-bit encrypted file is estimated to take more than a billion years to complete and a multi-million dollar budget to even start. Encryption is the easiest way to prevent a mobile device from becoming a liability later on.
2) Enable remote wiping
The next step in a cyber risk management plan is giving your organization the ability to wipe the memory and hard-drive on a device remotely. The ability to clear the device is critical in limiting the amount of time a hostile user would have to compromise sensitive data. Given the proper training and reporting procedures, the time an attacker would have to access the device drops significantly.
3) Limit information access
Compartmentalizing sensitive information is critical in limiting the scope of a breach. If possible, limit the amount of data each employee can access to only what is minimally required for that employee's day to day work.
4) Use multi-factor authentication
No organization is immune to phishing scams and employees reusing passwords. Setting your organization up for multi-factor authentication is critical in guarding against social engineering attacks. Multi-factor authentication requires the user to provide multiple pieces of evidence proving their identity. Requiring two forms of authentication (often a text message to the employee's phone) protects your emails and organization's data against intruders who might even have the log-in credentials or a stolen device.
5) Audit your system
No organization is perfect: technical and practical mistakes will happen that expose your organization to a data breach. Audits are critical in discovering those mistakes before a problem should arise.
6) Purchase a Cyber Insurance Policy
The final defense against a cyber intrusion should be a comprehensive cyber insurance policy. Claims data show that the average cost of a cyber attack is over $500,000, and the majority of those attacked are small to medium-sized businesses. Not only will the policy help you deal with the breach, but it will assist you in dealing with the aftermath of the attack to restore your organization.
About The Author: Austin Landes, CIC
Austin is an experienced Commercial Risk Advisor specializing in property & casualty risk management for religious institutions, real estate, construction, and manufacturing.
